Overview
One of the crucial vital issues for customers is cloud safety because of the rise in safety threats. Due to this fact, to safeguard the security of your deployed AWS sources, particular Id and Entry Administration (IAM) requirements have to be adopted. Whereas Buyer Dealt with Insurance policies, because the title suggests, are stand-alone insurance policies which might be maintained by customers of their separate AWS accounts, Managed Insurance policies are produced and managed by AWS. An IAM coveragegenerally known as aninline coverage` is built-in into the identification. When configuring the privileges for an identification in IAM, use a customer-controlled coverage or an inline coverage.
AWS Managed Insurance policies
An AWS-managed coverage is a stand-alone coverage that has been created and maintained by AWS. When a coverage is thought to be stand-alone, it signifies that its title seems in its personal distinctive Amazon Useful resource Title (ARN). One AWS-managed coverage is arn:aws:iam::was: coverage/IAMReadOnlyAccess. The IAMReadOnlyAccess AWS managed coverage offers read-only entry to all AWS companies and sources. When a service launches a brand new function, AWS provides read-only permissions for brand new operations and sources.
For a wide range of frequent-use eventualities, AWS-managed insurance policies are made to supply permissions. AWS-managed insurance policies for energy customers like AWSKeyManagementServicePowerUser and AWSCodeCommitPowerUser are created with their wants in thoughts. Assigning the right rights to customers, teams, and roles is extra simple when utilizing AWS-managed insurance policies than writing your insurance policies.
The insurance policies created for job capabilities are one form of AWS-managed particularly useful insurance policies. These rules intently match the duties carried out by typical IT employment roles. The objective is to make it easy to offer permissions for these typical job duties. An vital perk of working with AWS is that they keep and modify particular insurance policies as new companies and API actions are revealed.
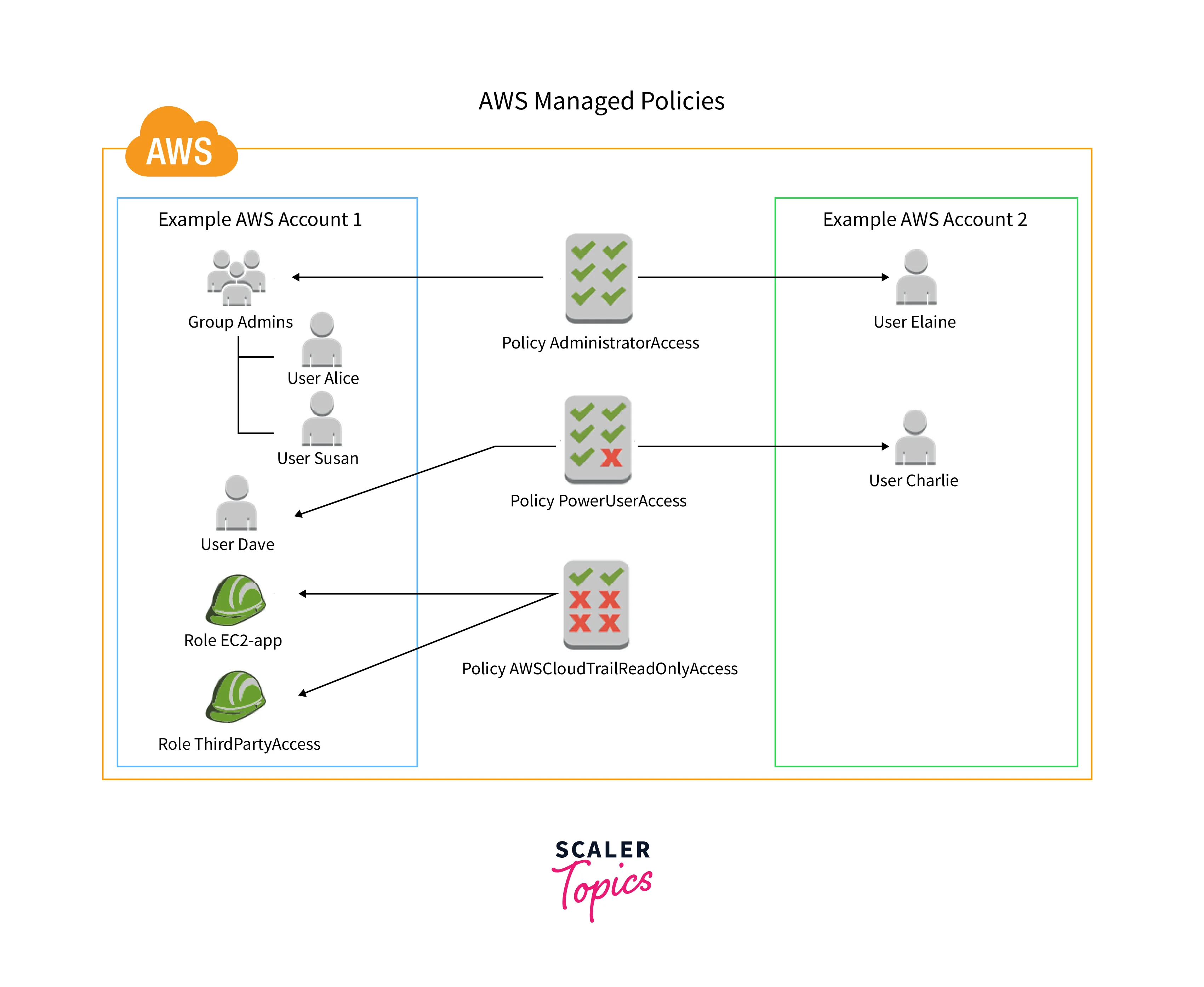
The permissions laid out in AWS-managed insurance policies can’t be altered. The permissions laid out in an AWS-managed coverage are periodically up to date by AWS. All principal entities (customers, teams, and roles) to whom the coverage is tied are impacted when AWS makes this modification. An AWS-managed coverage is most likely to be altered when a brand-new AWS service debut or when beforehand undocumented API strategies are made accessible for companies that presently exist.
As an illustration, all AWS companies and sources are accessible with read-only entry utilizing the AWS-managed coverage generally known as ReadOnlyAccess. AWS modifies the ReadOnlyAccess coverage so as to add read-only entry for a brand new service when it begins. The coverage’s connected major entities obtain the up to date permissions.
The diagram that follows reveals how AWS-managed insurance policies work. AdministratorAccess, PowerUserAccess, and AWSCloudTrailReadOnlyAccess are three examples of AWS-managed insurance policies which might be proven within the diagram. It is essential to grasp {that a} specific AWS-managed coverage will be carried out to the first models in each a single AWS account and quite a few distinct AWS accounts.
Buyer Managed Insurance policies
An impartial coverage that you simply design and handle within your personal AWS account is named a customer-managed coverage. Solely the customers, teams, and roles inside your account are eligible to have this coverage connected to them.
You possibly can duplicate a present AWS Managed Coverage and modify it to fulfill the wants of your corporation to construct a brand new Buyer Managed Coverage.

It’s suggested to make use of a customer-managed coverage in instances the place your setting’s necessities don’t match these of the already current AWS Managed Insurance policies.
Get Began Utilizing Permissions with AWS Managed Insurance policies
The most secure approach to grant the least privilege is to put in writing a customer-managed coverage with solely the skills wanted by your group. You have to set up a process that allows your crew to ask for extra permissions as wanted. It takes time and talent to create IAM customer-managed insurance policies that grant your crew solely the permissions they want.
Use AWS-managed insurance policies to start including permissions to your IAM identities (customers, consumer teams, and roles). Least privilege permissions usually are not granted below AWS-managed insurance policies. Should you present your principals larger permissions than they require to carry out the duties, you could consider the safety threat.
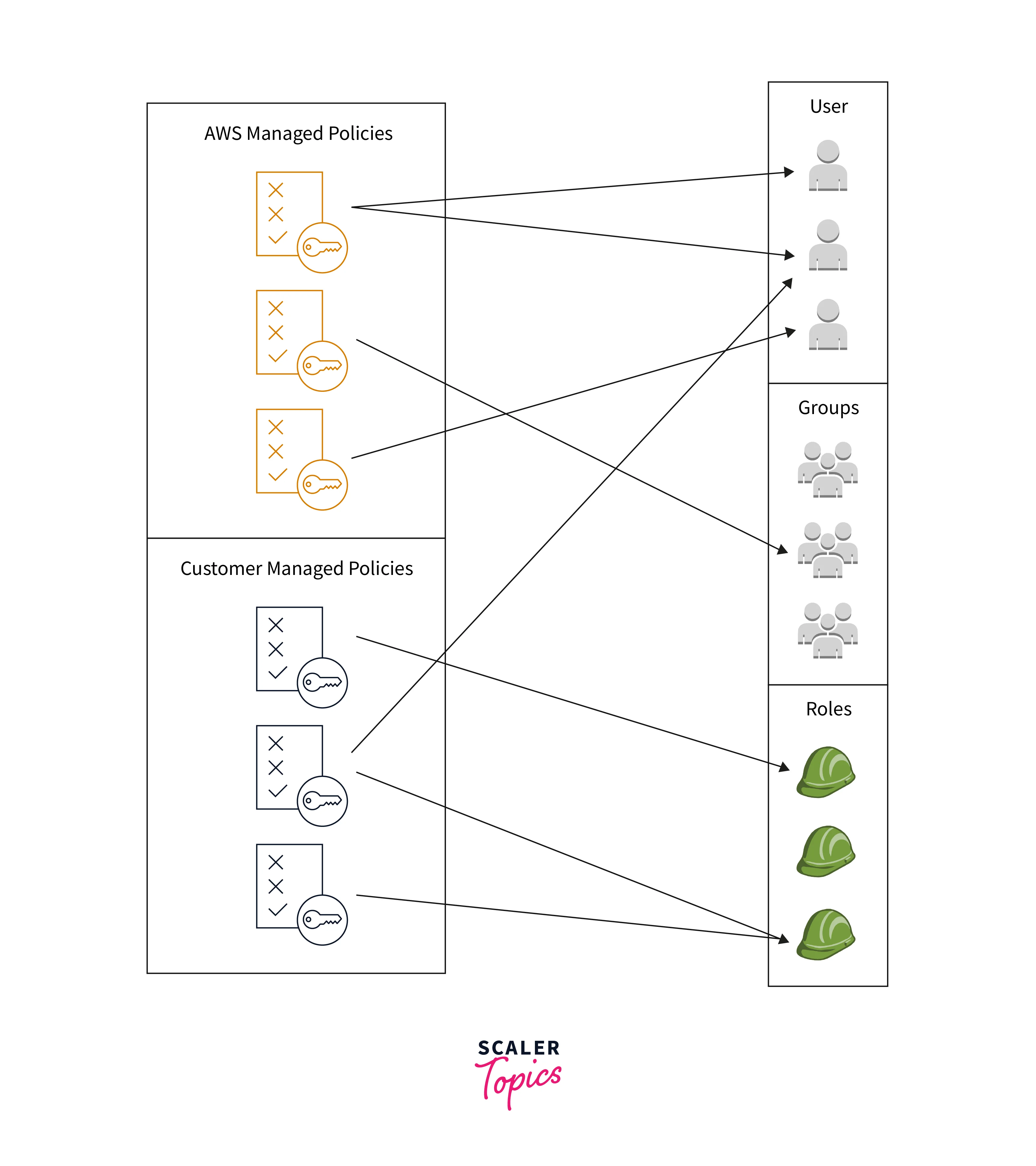
Any IAM identification can have AWS-managed insurance policies connected to it. Earlier than changing to least privilege permissions, you may observe the principals. As soon as you understand which permissions your crew is utilizing, it’s possible you’ll construct a customized coverage for them or a coverage with simply the permissions you want. That is much less safe however offers extra flexibility as you learn the way your crew is utilizing AWS.
Inline Insurance policies
An IAM coverage generally known as an Inline Coverage is built-in into the consumer, group, or position to which it’s relevant. The group and the coverage have a precise 1:1 relationship.
The coverage can be destroyed along with the consumer, group, or position that the inline coverage connected.
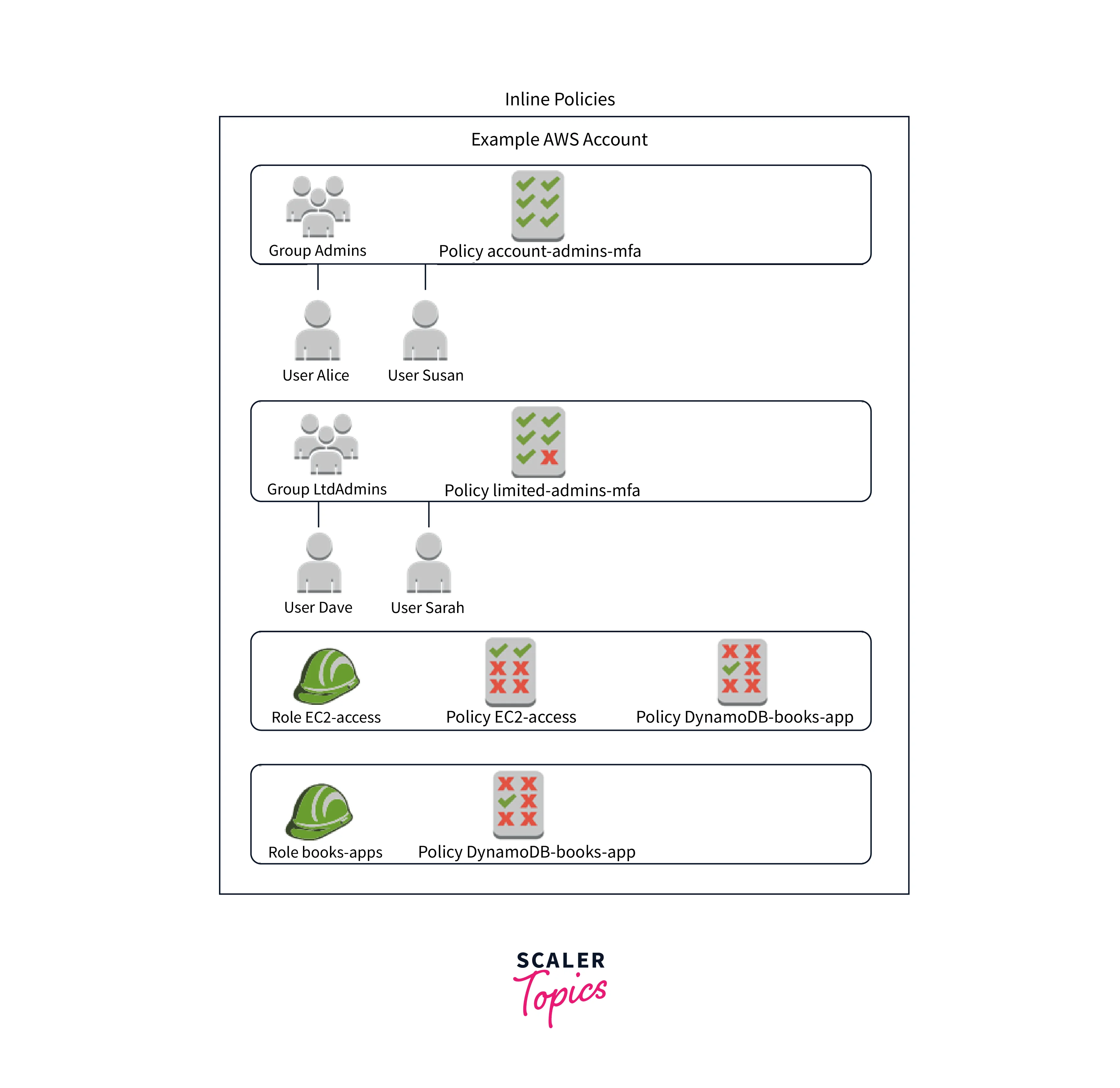
AWS sometimes advises selecting Managed Insurance policies over Inline Insurance policies.
Whenever you need to be sure that a coverage’s permissions usually are not unintentionally granted to every other customers, teams, or roles than those for which they’re meant, inline insurance policies may be useful (i.e. you might be establishing a coverage that may by no means be related to multiple consumer, group, or position).
Selecting Between Managed Insurance policies and Inline Insurance policies
The assorted coverage sorts will be chosen primarily based on the use case eventualities. We typically advise utilizing managed insurance policies reasonably than inline insurance policies.
The options listed under are provided by managed insurance policies:
- Reusability: A number of principal entities could also be linked to a single managed coverage (customers, teams, and roles). It’s possible you’ll, in essence, compile a set of insurance policies that specify the permissions you will want to your AWS account, and you may then connect these guidelines to major entities as crucial.
- Central Change Administration: All major entities with which the managed coverage is related are affected whenever you make a change to it. As an illustration, you possibly can edit the managed coverage to incorporate the permission for those who wished so as to add it for a brand new AWS API. All main entities to whom the coverage is said can be affected when it’s modified. In distinction, it’s a must to individually modify every identification that the inline coverage is contained in if you wish to change it. As an illustration, if an inline coverage is shared by a bunch and a task, you could manually edit every of the `two main components to change it.
- Versioning and Rolling Again: Whenever you alter a customer-managed coverage, the brand new model would not change the previous one. IAM as a substitute develops a recent iteration of the managed coverage. Your customer-managed insurance policies could also be saved in as much as 5 totally different variations by IAM. If crucial, you may return to a earlier model of a coverage utilizing coverage variations.
- Delegating Permissions Administration: Whereas maintaining management over the rights outlined in these insurance policies, you may allow customers in your AWS account to connect and detach insurance policies. You possibly can basically designate choose folks as full directors, or directors who can add, edit, and take away insurance policies. Then, you may assign different customers as restricted directors. Directors can solely connect these insurance policies to different major organizations, that you’ve given them permission to.
- Automated Updates for AWS Managed Insurance policies: With out your involvement, AWS retains observe of AWS managed insurance policies and modifies them as wanted (as an example, so as to add permissions for brand new AWS companies). The first entities to whom you’ve got linked the AWS-managed coverage mechanically obtain the updates.
Changing an Inline Coverage to a Managed Coverage
You possibly can change any inline insurance policies you’ve got in your account to managed insurance policies. You possibly can duplicate the coverage to a newly managed coverage to perform this. The brand new coverage ought to then be linked to the identification that already has the inline coverage. After that, take away the inline coverage. The steps listed under can be utilized to do that.
Technique of Altering an Inline Coverage Right into a Managed Coverage
- Open the IAM console by logging into the AWS Administration Console at this Link.
- You possibly can choose Person teams, Customers, or Roles from the navigation pane.
- Choose the title of the consumer group, consumer, or position that’s the proprietor of the coverage you need to delete from the checklist.
- Choose the Permissions tab.
- Select the title of the inline coverage you need to delete for consumer teams. If crucial, choose Present n extra for customers and roles earlier than choosing the arrow beside the inline coverage you want to delete.
- For the coverage, replicate the JSON coverage doc.
- Choose `Insurance policies from the navigation window.
- Choose the JSON tab after choosing Create coverage.
- Choose Person Teams, Customers, or Roles from the navigation pane, then click on the title of the consumer group, consumer, or position that has the coverage you want to delete.
- Choose Add permissions below Customers and Roles.
- Examine the field beside the title of your new coverage, choose Add permissions, after which choose Connect a coverage for consumer teams. Add permissions will be chosen for folks or roles. Choose Subsequent: Evaluation, examine the field beside the title of your new coverage, choose Connect current insurance policies immediately, after which choose Add permissions.
- Your consumer group, consumer, or position’s abstract web page is displayed as soon as extra.
- The inline coverage is now deleted and an identical managed coverage has been connected to the useful resource with the identical permissions.
Deprecated AWS Managed Insurance policies
When a brand new service is added, AWS could must replace an previous coverage with new permission. There aren’t any options or talents disrupted or misplaced when new permission is added to an current coverage.
Nonetheless, if the required modifications to a present coverage may have an effect on clients, AWS can resolve to develop a brand new coverage as a substitute. As an illustration, deleting permissions from a longtime coverage might have an effect on all IAM entities and functions that depend on it, thereby disrupting a vital course of.
The traits of a deprecated coverage are as follows:
- It nonetheless capabilities for all customers, teams, and roles which might be presently related. Nothing is damaged.
- It’s incompatible with any brand-new customers, teams, or roles. It can’t be reattached to an current entity as soon as it has been indifferent.
- It turns into invisible and utterly ineffective upon getting indifferent it from all lively entities.
Instead, you could connect the brand new coverage if any consumer, group, or position nonetheless wants the previous one. We advise that, as quickly as you study {that a} coverage is being deprecated, you make plans to promptly detach all customers, teams, and roles from the deprecated coverage and fasten them to the alternative. The hazards related to utilizing the deprecated coverage can solely be eradicated by altering to the alternative coverage.
Conclusion
- An IAM coverage that’s produced and managed by AWS is named an AWS Managed Coverage. Based mostly on the duty, AWS gives Managed Insurance policies for fashionable eventualities.
- An impartial coverage that you simply design and handle within your personal AWS account is named a customer-managed coverage. Solely the customers, teams, and roles inside your account are eligible to have this coverage connected to them.
- An IAM coverage generally known as an Inline Coverage is built-in into the consumer, group, or place to which it’s relevant. The group and the coverage have a precise 1:1 relationship.
- You possibly can change any inline insurance policies you’ve got in your account to managed insurance policies. Replicate the coverage with a newly managed coverage to perform this. Put the brand new coverage on the identification that already has the inline coverage. After that, take away the inline coverage.
- AWS retains observe of the AWS-managed insurance policies and updates them mechanically. The earlier coverage is then designated as deprecated. Within the IAM console’s Insurance policies checklist, a deprecated managed coverage has a warning icon subsequent to it.


