Overview
AWS Identification and Entry Administration (IAM) controls entry to AWS providers and sources. It consists of customers, teams, roles, insurance policies, and permissions. Customers are entities with distinctive credentials, whereas teams set up customers for collective permission administration. Roles outline permissions for entities each inside and out of doors AWS accounts. Insurance policies are JSON paperwork outlining permissions, connected to customers, teams, or roles. IAM ensures safety by regulating who can entry sources and what actions they will carry out, facilitating granular management over AWS providers, minimizing safety dangers, and permitting scalable, safe administration of customers’ entry inside the AWS ecosystem.
What are IAM Parts in AWS?

IAM parts are the elemental parts and ideas inside IAM that allow you to handle entry to your AWS atmosphere.
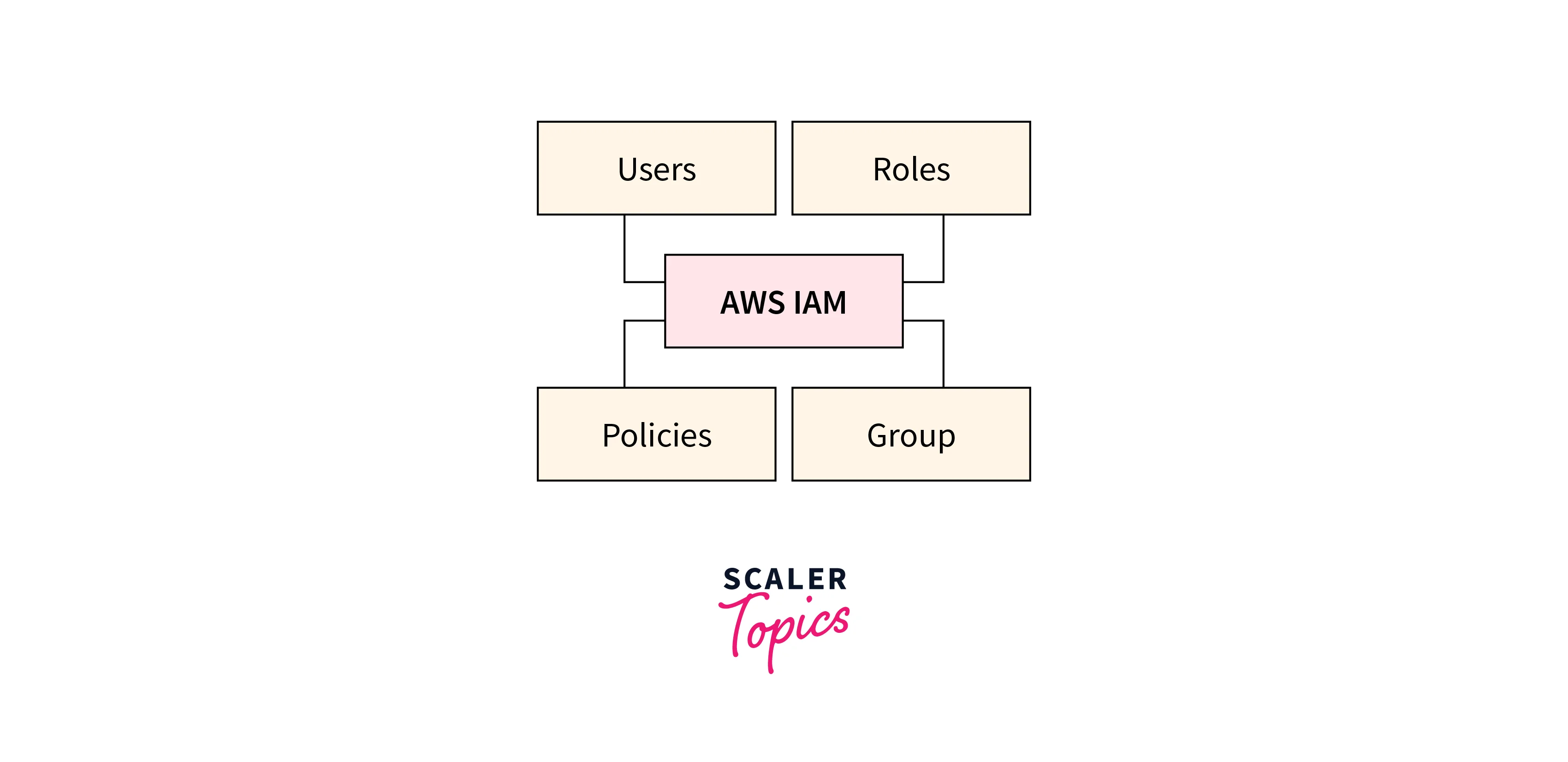
Customers
IAM customers in AWS are elementary entities representing people, functions, or providers interacting with AWS sources. Every person has distinct credentials—username/password or entry keys—enabling entry to the AWS Administration Console or programmatic interplay by way of APIs. Customers are pivotal in entry management, the place permissions are assigned by insurance policies defining allowable actions on particular AWS sources. This granularity permits adherence to safety greatest practices, like implementing Multi-Issue Authentication (MFA) and following the precept of least privilege. Person lifecycle administration includes creation, modification, and deletion as organizational wants evolve.
Customers can assume roles to combine with different AWS providers briefly, facilitating duties or useful resource entry. For Instance, “Sameer” is an IAM person with rights to handle S3 buckets and restricted entry to EC2 situations.
Teams
In AWS IAM Parts, Teams are collections of IAM customers, simplifying permission administration by permitting bulk project of insurance policies. They function a strategy to set up customers with related tasks or entry necessities into logical models. By associating insurance policies with teams, permissions may be effectively granted or revoked throughout a number of customers concurrently. This streamlines administration, guaranteeing constant entry controls for customers inside the identical practical or departmental position.
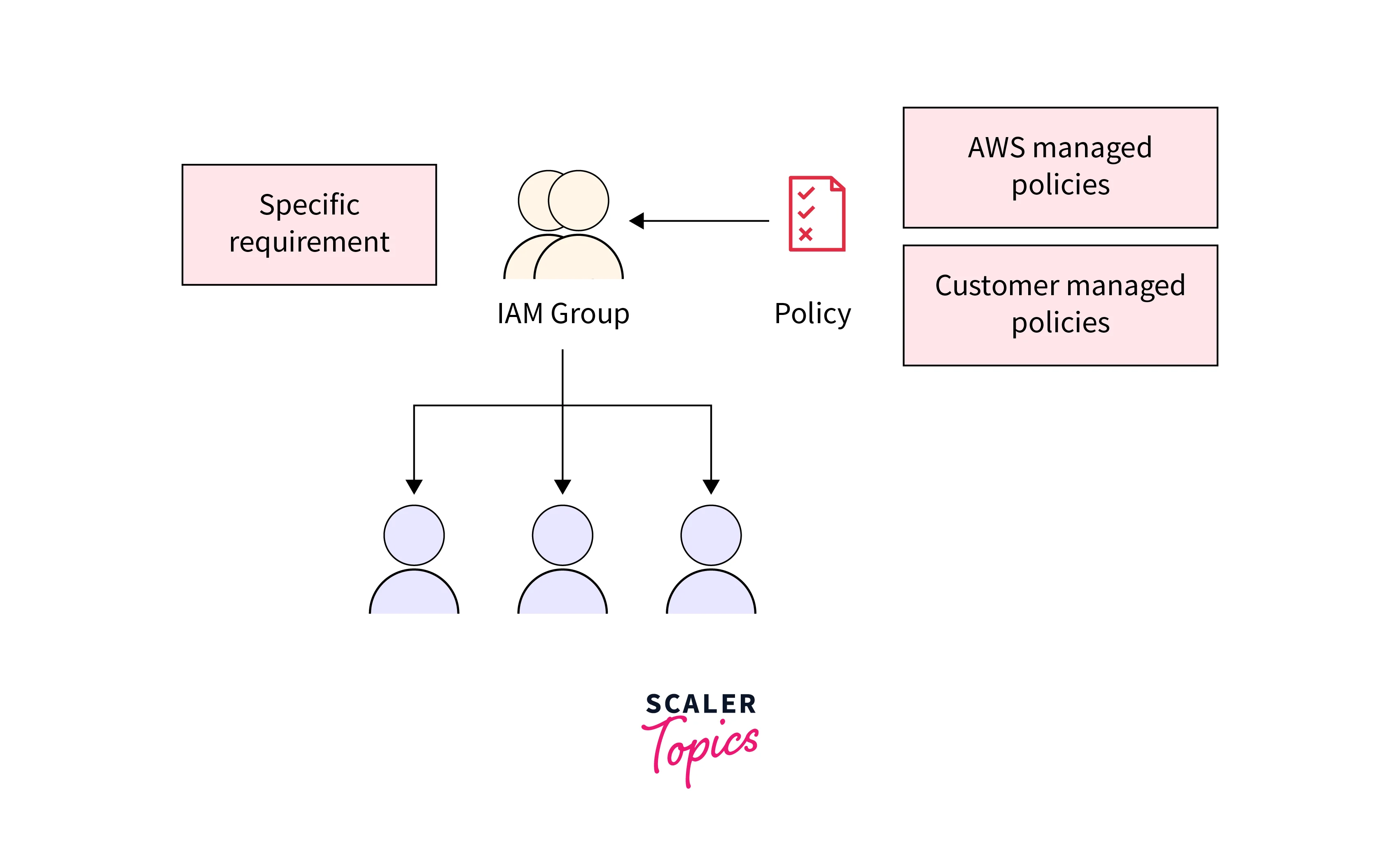
Teams haven’t got their very own credentials; they inherit permissions from the insurance policies connected to them. This abstraction minimizes redundancy, as adjustments made to group insurance policies mirror in all related customers’ permissions. Teams improve safety by imposing the precept of least privilege, granting customers solely the mandatory entry for his or her roles. For instance, the “Builders” group may need entry to EC2 situations and restricted rights to handle S3 buckets.
Roles
In AWS IAM, Roles are pivotal parts designed for interplay between AWS providers and functions with different AWS sources. Not like customers, roles usually are not immediately related to particular people or entities; as a substitute, they’re meant for momentary use by automated programs. Roles provide a safe and versatile mechanism for delegated permissions, broadly employed by providers corresponding to EC2 situations and Lambda capabilities. When a service assumes a job, it beneficial properties momentary entry to specified sources, guaranteeing accountability and traceability.
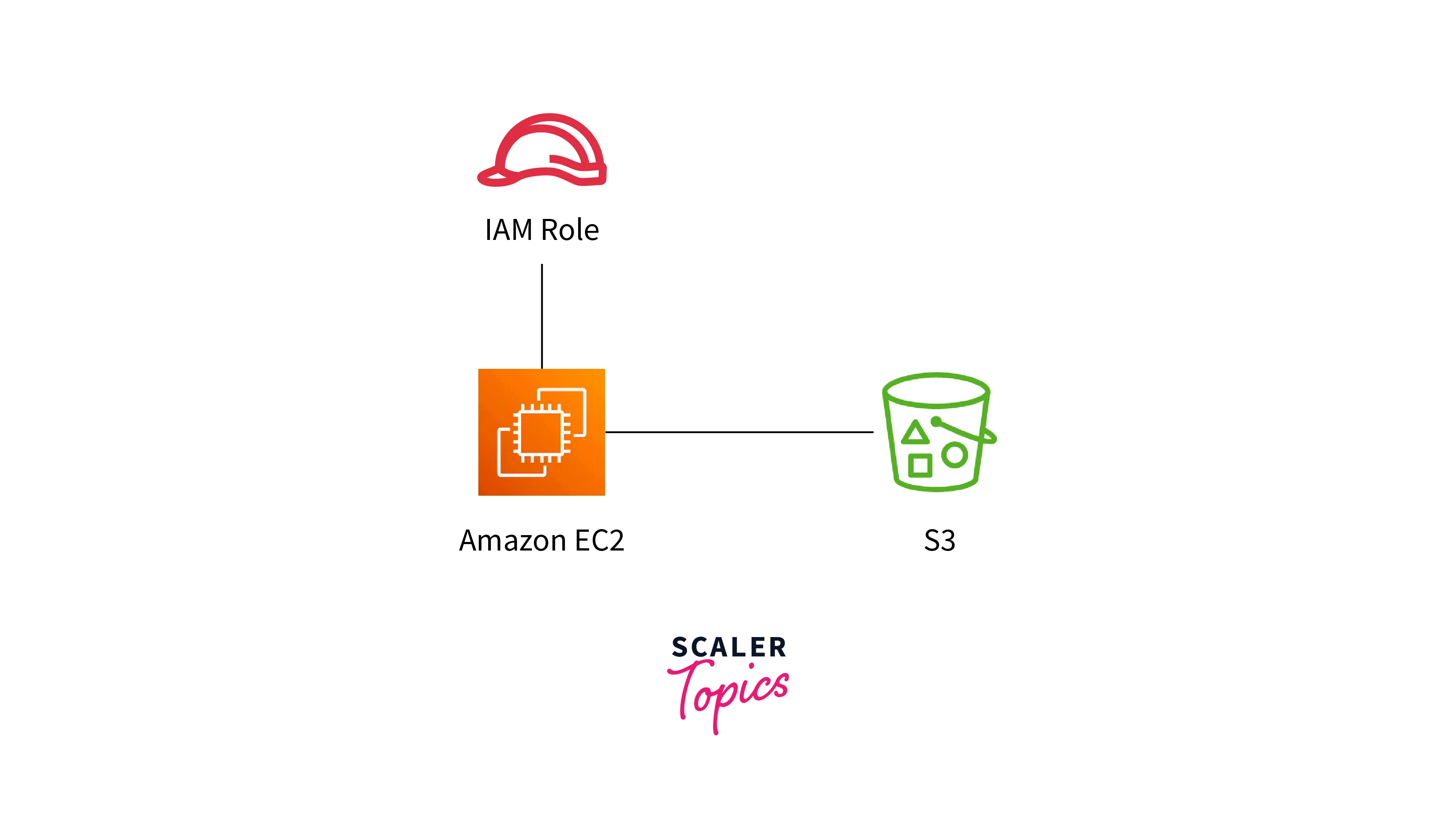
Roles play an important position in enabling fine-grained entry management and adhering to the precept of least privilege. They facilitate safe delegation of permissions, permitting providers to carry out vital duties with out the constraints of everlasting id associations, thereby enhancing flexibility, safety, and governance inside the AWS atmosphere. For instance, “DataAnalystRole” grants read-only entry to S3 buckets and permits working particular queries inside an RDS database, guaranteeing managed information evaluation.
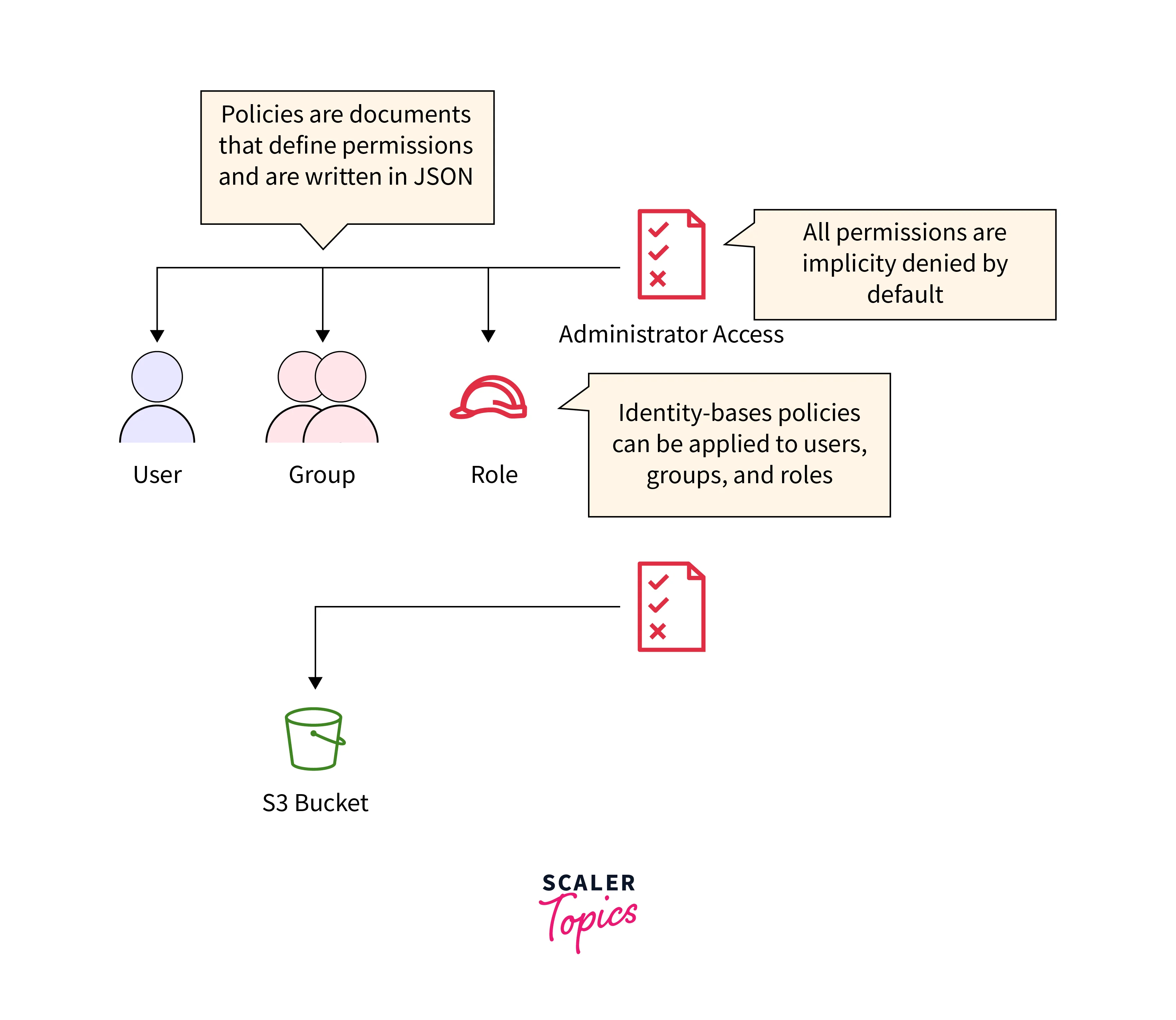
Insurance policies
In AWS IAM, insurance policies are essential parts defining permissions and entry controls for customers, teams, and roles. These JSON-based paperwork define guidelines specifying what actions are permitted or denied on particular AWS sources. Insurance policies may be connected to IAM identities, permitting exact definition of allowed actions, sources, and circumstances for entry. They embody statements that articulate permissions, together with actions (corresponding to learn, write, or modify), sources (like S3 buckets or EC2 situations), and optionally available circumstances (like IP addresses or time of entry).
Insurance policies allow the implementation of the precept of least privilege, guaranteeing that entities have solely the mandatory permissions for his or her duties, bolstering safety and compliance. This coverage grants permission to carry out the s3:GetObject motion on all objects inside the “example-bucket” S3 bucket (arn:aws:s3:::example-bucket/*)
IAM Processes
IAM (Identification and Entry Administration) processes are essential for managing and controlling entry to sources inside a corporation’s digital atmosphere.
Authentication
- Authentication inside IAM processes includes verifying a person’s id to grant entry to programs or sources.
- It is the essential step the place people show they’re who they declare to be.
- Numerous strategies guarantee this verification, together with passwords, biometrics (like fingerprints or facial recognition), tokens, or sensible playing cards.
- Multi-factor authentication (MFA) combines two or extra authentication elements for heightened safety.
- The method includes validating the offered credentials towards saved or generated information, guaranteeing their accuracy earlier than allowing entry.
- Strong authentication mechanisms thwart unauthorized entry makes an attempt, enhancing system safety.
- Continuous developments in know-how, corresponding to adaptive authentication, analyze a number of elements like location, system, and habits to dynamically regulate safety measures.
- Authentication, a cornerstone of IAM, safeguards delicate data and sources whereas enabling professional customers to entry important programs effectively.
Authorization
- Authorization inside IAM processes dictates the permissions and degree of entry granted to authenticated customers.
- As soon as a person’s id is confirmed by authentication, authorization determines what sources, information, or actions they will entry or carry out inside a system or utility.
- This course of includes defining person roles, teams, or particular person entitlements and associating them with particular permissions or restrictions.
- Entry management lists (ACLs), role-based entry management (RBAC), attribute-based entry management (ABAC), or different mechanisms are employed to implement these authorizations.
- Authorization ensures that customers solely have entry to the sources required for his or her roles whereas stopping unauthorized entry to delicate information or essential programs.
- Steady monitoring and periodic critiques of authorization settings are important to take care of safety, compliance, and alignment with evolving organizational wants inside the IAM framework.
Identification Lifecycle Administration
- Identification Lifecycle Administration (ILM) in IAM processes includes the excellent administration of person identities all through their complete lifecycle inside a corporation.
- This encompasses the creation, modification, and deactivation of person accounts, aligning entry with their evolving roles and tasks.
- Throughout onboarding, ILM ensures the provisioning of applicable entry rights.
- All through a person’s tenure, it facilitates updates and changes to permissions based mostly on altering roles or necessities.
- When staff depart, ILM oversees the deprovisioning course of, promptly revoking entry to stop safety dangers.
- Automation performs a key position in streamlining these processes, enhancing effectivity, and lowering the danger of human error.
- Efficient ILM contributes to safety, compliance, and operational effectivity, making it an important element of IAM methods for organizations managing entry to digital sources.
Person Administration
In Amazon Internet Providers (AWS), Identification and Entry Administration (IAM) governs Person Administration, enabling the management and administration of person entry to AWS sources. Inside AWS IAM, Person Administration includes a number of key elements:
- Person Creation and Deletion:
IAM permits the creation of particular person customers or teams, every with distinctive credentials and permissions tailor-made to particular roles or duties. Admins can swiftly create, modify, or delete person accounts as wanted. - Permission Project:
Customers are granted permissions by way of insurance policies. These insurance policies outline what actions they will carry out on AWS sources. Permissions may be granular, permitting exact management over useful resource entry. - Multi-factor Authentication (MFA):
IAM helps MFA, including an additional layer of safety by requiring customers to current a further type of verification, corresponding to a code from a cellular system, together with their password. - Password Insurance policies:
Directors can set and implement password insurance policies to make sure sturdy, repeatedly up to date passwords for person accounts, bolstering safety measures. - Entry Keys and Credentials:
IAM manages entry keys for programmatic entry to AWS providers, permitting automation and interplay with AWS sources by APIs securely.
IAM Finest Practices
Precept of Least Privilege (PoLP)
The Precept of Least Privilege (PoLP) in AWS IAM is a core greatest observe that advocates granting customers solely the minimal permissions required to carry out their duties. It ensures that customers have exactly the mandatory entry rights and no extra, minimizing the potential influence of safety breaches or human errors. By following PoLP, AWS IAM assigns permissions at a granular degree, tailoring entry to particular job roles or capabilities.
Recurrently reviewing and refining these permissions helps to align entry with evolving tasks, lowering the danger of unauthorized actions or information breaches. Implementing PoLP enhances safety by limiting the scope of potential injury from compromised accounts, lowering assault surfaces, and enabling higher management over AWS sources, guaranteeing a extra strong and safe atmosphere.
Multi-Issue Authentication (MFA) Authentication Strategies
Multi-Issue Authentication (MFA) is a vital greatest observe inside AWS Identification and Entry Administration (IAM) that provides an additional layer of safety past passwords. AWS encourages MFA as a typical authentication methodology for person accounts. It requires customers to current at the very least two types of verification earlier than accessing AWS sources, usually combining one thing they know (like a password) with one thing they’ve (corresponding to a cellular system or {hardware} token).
By implementing MFA in AWS IAM, it considerably reduces the danger of unauthorized entry, even when passwords are compromised. AWS helps numerous MFA strategies like digital MFA gadgets, {hardware} MFA tokens, or SMS-based authentication, permitting customers flexibility in selecting their most popular authentication mechanism. Imposing MFA throughout person accounts strengthens safety measures, aligning with trade greatest practices and bolstering safety towards unauthorized entry makes an attempt inside the AWS atmosphere.
Common Auditing
Common auditing in AWS IAM is a elementary greatest observe that includes systematically reviewing and analyzing person permissions, entry logs, and configurations inside an AWS atmosphere. This course of ensures compliance adherence, identifies safety gaps, and detects any unauthorized or suspicious actions. Auditing includes scrutinizing entry controls, IAM insurance policies, and person actions to confirm that permissions align with the Precept of Least Privilege and adjust to organizational requirements and rules.
By routinely analyzing IAM configurations and entry logs, organizations can proactively deal with vulnerabilities, stop unauthorized entry, and reply swiftly to potential safety incidents. This observe enhances the general safety posture, aids in threat mitigation, helps compliance necessities, and fosters a proactive safety method, enabling organizations to take care of a sturdy and safe AWS atmosphere.
Conclusion
- AWS IAM parts embrace customers, teams, roles, insurance policies, ACLs, MFA, Identification Suppliers, STS, credential experiences, entry analyzer, and greatest practices analyzer, managing entry and permissions inside AWS.
- IAM Customers are entities with distinctive credentials inside AWS, permitting people to work together with AWS providers, every having outlined permissions and entry to sources.
- IAM Teams in AWS are collections of customers sharing related permissions. They simplify entry administration by permitting insurance policies to be utilized collectively to a number of customers.
- IAM Roles in AWS grant momentary permissions for customers, providers, or sources, defining entry to particular AWS sources with no need everlasting credentials.
- IAM Insurance policies in AWS outline permissions, permitting or denying actions on particular AWS sources. They’re connected to customers, teams, or roles, controlling entry inside the AWS atmosphere.
- Authentication in AWS IAM verifies person identities utilizing credentials like passwords or keys, guaranteeing entry to AWS providers aligns with licensed customers.
- Authorization in AWS IAM controls person entry to AWS sources by making use of insurance policies defining what actions are permitted or denied based mostly on outlined permissions and roles.
- Identification Lifecycle Administration in AWS IAM includes managing person identities all through their complete tenure, protecting creation, modification, and deactivation to align entry with evolving roles and necessities.
- IAM greatest practices in AWS contain implementing least privilege, utilizing MFA, repeatedly auditing permissions, creating and managing roles, and using sturdy insurance policies for safe entry administration.


