To ensure that a person to carry out an motion (equivalent to itemizing, modifying or
deleting elements of a VM’s configuration), the person must have the
acceptable permissions.
Proxmox VE makes use of a job and path based mostly permission administration system. An entry in
the permissions desk permits a person, group or token to tackle a selected function
when accessing an object or path. Which means that such an entry rule can
be represented as a triple of (path, person, function), (path, group,
function) or (path, token, function), with the function containing a set of allowed
actions, and the trail representing the goal of those actions.
Roles
A task is solely an inventory of privileges. Proxmox VE comes with a quantity
of predefined roles, which fulfill most necessities.
-
Administrator: has full privileges -
NoAccess: has no privileges (used to forbid entry) -
PVEAdmin: can do most duties, however has no rights to switch system settings
(Sys.PowerMgmt, Sys.Modify, Realm.Allocate) or permissions
(Permissions.Modify) -
PVEAuditor: has learn solely entry -
PVEDatastoreAdmin: create and allocate backup house and templates -
PVEDatastoreUser: allocate backup house and consider storage -
PVEMappingAdmin: handle useful resource mappings -
PVEMappingUser: view and use useful resource mappings -
PVEPoolAdmin: allocate swimming pools -
PVEPoolUser: view swimming pools -
PVESDNAdmin: handle SDN configuration -
PVESDNUser: entry to bridges/vnets -
PVESysAdmin: audit, system console and system logs -
PVETemplateUser: view and clone templates -
PVEUserAdmin: handle customers -
PVEVMAdmin: totally administer VMs -
PVEVMUser: view, backup, configure CD-ROM, VM console, VM energy administration
You may see the entire set of predefined roles within the GUI.
You may add new roles through the GUI or the command line.
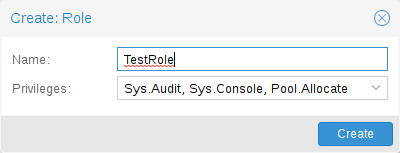
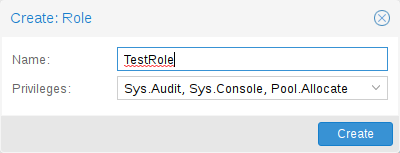
From the GUI, navigate to the Permissions → Roles tab from Datacenter and
click on on the Create button. There you possibly can set a job identify and choose any
desired privileges from the Privileges drop-down menu.
So as to add a job by the command line, you need to use the pveum CLI device, for
instance:
pveum function add VM_Power-only --privs "VM.PowerMgmt VM.Console" pveum function add Sys_Power-only --privs "Sys.PowerMgmt Sys.Console"
|
|
Roles beginning with PVE are at all times builtin, customized roles will not be
allowed use this reserved prefix. |
Privileges
A privilege is the precise to carry out a selected motion. To simplify
administration, lists of privileges are grouped into roles, which might then
be used within the permission desk. Observe that privileges can’t be instantly
assigned to customers and paths with out being a part of a job.
We presently assist the next privileges:
-
Node / System associated privileges -
-
Group.Allocate: create/modify/take away teams -
Mapping.Audit: view useful resource mappings -
Mapping.Modify: handle useful resource mappings -
Mapping.Use: use useful resource mappings -
Permissions.Modify: modify entry permissions -
Pool.Allocate: create/modify/take away a pool -
Pool.Audit: view a pool -
Realm.AllocateUser: assign person to a realm -
Realm.Allocate: create/modify/take away authentication realms -
SDN.Allocate: handle SDN configuration -
SDN.Audit: view SDN configuration -
Sys.Audit: view node standing/config, Corosync cluster config, and HA config -
Sys.Console: console entry to node -
Sys.Incoming: permit incoming information streams from different clusters (experimental) -
Sys.Modify: create/modify/take away node community parameters -
Sys.PowerMgmt: node energy administration (begin, cease, reset, shutdown, …) -
Sys.Syslog: view syslog -
Consumer.Modify: create/modify/take away person entry and particulars.
-
-
Digital machine associated privileges -
-
SDN.Use: entry SDN vnets and native community bridges -
VM.Allocate: create/take away VM on a server -
VM.Audit: view VM config -
VM.Backup: backup/restore VMs -
VM.Clone: clone/copy a VM -
VM.Config.CDROM: eject/change CD-ROM -
VM.Config.CPU: modify CPU settings -
VM.Config.Cloudinit: modify Cloud-init parameters -
VM.Config.Disk: add/modify/take away disks -
VM.Config.HWType: modify emulated {hardware} sorts -
VM.Config.Reminiscence: modify reminiscence settings -
VM.Config.Community: add/modify/take away community units -
VM.Config.Choices: modify some other VM configuration -
VM.Console: console entry to VM -
VM.Migrate: migrate VM to alternate server on cluster -
VM.Monitor: entry to VM monitor (kvm) -
VM.PowerMgmt: energy administration (begin, cease, reset, shutdown, …) -
VM.Snapshot.Rollback: rollback VM to one among its snapshots -
VM.Snapshot: create/delete VM snapshots
-
-
Storage associated privileges -
-
Datastore.Allocate: create/modify/take away a datastore and delete volumes -
Datastore.AllocateSpace: allocate house on a datastore -
Datastore.AllocateTemplate: allocate/add templates and ISO photographs -
Datastore.Audit: view/browse a datastore
-
|
|
Each Permissions.Modify and Sys.Modify must be dealt with with
care, as they permit modifying facets of the system and its configuration that are harmful or delicate. |
|
|
Fastidiously learn the part about inheritance under to grasp how
assigned roles (and their privileges) are propagated alongside the ACL tree. |
Objects and Paths
Entry permissions are assigned to things, equivalent to digital machines,
storages or useful resource swimming pools.
We use file system like paths to handle these objects. These paths type a
pure tree, and permissions of upper ranges (shorter paths) can
optionally be propagated down inside this hierarchy.
Paths might be templated. When an API name requires permissions on a
templated path, the trail could comprise references to parameters of the API
name. These references are laid out in curly braces. Some parameters are
implicitly taken from the API name’s URI. As an illustration, the permission path
/nodes/{node} when calling /nodes/mynode/standing requires permissions on
/nodes/mynode, whereas the trail {path} in a PUT request to /entry/acl
refers back to the technique’s path parameter.
-
/nodes/{node}: Entry to Proxmox VE server machines -
/vms: Covers all VMs -
/vms/{vmid}: Entry to particular VMs -
/storage/{storeid}: Entry to a selected storage -
/pool/{poolname}: Entry to sources contained in a selected pool -
/entry/teams: Group administration -
/entry/realms/{realmid}: Administrative entry to realms
Inheritance
As talked about earlier, object paths type a file system like tree, and
permissions might be inherited by objects down that tree (the propagate flag is
set by default). We use the next inheritance guidelines:
-
Permissions for particular person customers at all times change group permissions. -
Permissions for teams apply when the person is member of that group. -
Permissions on deeper ranges change these inherited from an higher degree. -
NoAccess cancels all different roles on a given path.
Moreover, privilege separated tokens can by no means have permissions on any
given path that their related person doesn’t have.
Swimming pools
Swimming pools can be utilized to group a set of digital machines and datastores. You may
then merely set permissions on swimming pools (/pool/{poolid}), that are inherited by
all pool members. It is a nice technique to simplify entry management.
Which Permissions Do I Want?
The permissions are specified as an inventory, which might be interpreted as a
tree of logic and access-check capabilities:
-
["and", <subtests>...] and ["or", <subtests>...] -
Every(and) or any(or) additional component within the present checklist needs to be true. -
["perm", <path>, [ <privileges>... ], <choices>...] -
The path is a templated parameter (see
Objects and Paths). All (or, if the any
possibility is used, any) of the listed
privileges have to be allowed on the desired path. If a require-param
possibility is specified, then its specified parameter is required even when the
API name’s schema in any other case lists it as being optionally available. -
["userid-group", [ <privileges>... ], <choices>...] -
The caller will need to have any of the listed privileges on /entry/teams. In
addition, there are two potential checks, relying on whether or not the
groups_param possibility is about:-
groups_param is about: The API name has a non-optional teams parameter
and the caller will need to have any of the listed privileges on all the listed
teams. -
groups_param just isn’t set: The person handed through the userid parameter
should exist and be a part of a gaggle on which the caller has any of the listed
privileges (through the /entry/teams/<group> path).
-
-
["userid-param", "self"] -
The worth offered for the API name’s userid parameter should discuss with the
person performing the motion (often along side or, to permit
customers to carry out an motion on themselves, even when they don’t have elevated
privileges). -
["userid-param", "Realm.AllocateUser"] -
The person wants Realm.AllocateUser entry to /entry/realm/<realm>, with
<realm> referring to the realm of the person handed through the userid
parameter. Observe that the person doesn’t have to exist so as to be
related to a realm, since person IDs are handed within the type of
<username>@<realm>. -
["perm-modify", <path>] -
The path is a templated parameter (see
Objects and Paths). The person wants both the
Permissions.Modify privilege or,
relying on the trail, the next privileges as a potential substitute:-
/storage/...: requires ‘Datastore.Allocate` -
/vms/...: requires ‘VM.Allocate` -
/pool/...: requires ‘Pool.Allocate`If the trail is empty, Permissions.Modify on /entry is required.
If the person doesn’t have the Permissions.Modify privilege, they will solely
delegate subsets of their very own privileges on the given path (e.g., a person with
PVEVMAdmin may assign PVEVMUser, however not PVEAdmin).
-